IT Articles

IT Articles
IT Articles

Recently, a client told us, “We have experienced a significant change in our service desk experience,” which made our day! You may have also noticed similar improvements in your interactions with our service desk. Internally, we have reorganized the Service Desk team around a goal we call First-Contact Resolution (FCR). In short, we aim to address your issue the first time you contact us as often as possible. Here’s how our commitment to FCR can transform your support experience and provide tangible benefits for your business. Benefits of FCR for You: Faster Response Times:…

Two major email communication players, Yahoo and Google, have recently implemented significant changes in their approach to bulk email sending. These adjustments aim to enhance user experience, improve email deliverability, and combat spam. In this article, we will explore the key modifications made by both Yahoo and Google, shedding light on their implications for email marketers and the broader digital community. Google’s Changes: Google has rolled out updates designed to create a more secure and user-friendly environment. One of the notable changes is the introduction of BIMI (Brand Indicators for Message Identification), which allows…

Credit Union Cybersecurity Threats Cyberattacks are one of the greatest threats financial institutions face. The average financial security breach costs approximately $5.97 million. For credit union cybersecurity, this means keeping up to date with the latest cyber solutions is critical to protecting member data and their good name. On average, financial risk can range from $190,000 for a small to mid-size credit union up to $1.2 million for large credit unions. Assessing potential cyber threats will allow you to adjust your IT infrastructure accordingly. Below we break down specific threats and what you can…

Effective September 1, 2023, the NCUA will require all federally insured credit unions to notify the NCUA as soon as possible, within 72 hours after a reportable cyber incident has occurred. “Each of us in the financial system has an obligation to protect our nation’s economic and financial infrastructure. And, credit unions must be included in conversations about critical infrastructure, as a whole. This final rule will facilitate such dialogue,” Chairman Todd M. Harper said. “Through these high-level early warning notifications, the NCUA will be able to work with other agencies and the private…

It is common for businesses to assume an internal staff will always be the best choice without considering the benefits of outsourcing to a group with a wide range of experience and skills, as well as, extensive knowledge. While there are certain benefits of having an internal staff, this article aims to highlight specific benefits of working with a managed IT service provider that should be considered. We often get asked, “Why should I work with an IT provider that is not onsite, when I can hire an internal IT guy?” It is a…

What is Hardware as a Service? Hardware as a Service (HaaS) is a subscription model that provides software and hardware as a monthly service. Clients can gain access to new hardware by paying a monthly subscription fee instead of investing large amounts of capital outright. The equipment is procured and installed by a managed IT service provider (MSP) and a service level agreement (SLA) is put in place to clearly define both the MSP and the client’s ongoing responsibilities. Hardware as a Service helps your business acquire the necessary technology and when combined with…

As a local Savannah managed service provider, our priority is to ensure all businesses achieve a more secure, stable, and reliable IT environment. We achieve this through 24x7x365 monitoring and alerting. We work to keep your network running at all times to help reduce the cost of unexpected downtime. Selecting your local managed service provider doesn’t have to be difficult. Below we will breakdown how we can best serve your organization. Dynamic Quest Can Be Your Savannah Managed IT Service Provider Our team focuses on being a strategic technology partner with your organization. We…

Manufacturers continue to adopt new technologies as their business models evolve. They may be dealing with production issues, supply chain challenges, regulatory compliance or logistic complications, all things that directly deal with their internal IT business systems. Working with a managed service provider, businesses can identify specific IT solutions for manufacturing. They will be able to implement IT solutions specific to manufacturing that build a secure and reliable network that continues to grow for the long term. If you are curious to learn more about manufacturing IT support, including the benefits of working with…
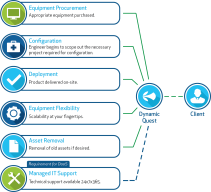
Regardless of your company’s size, upgrading your technology equipment (Servers, workstations, switches, firewalls, SAN) every three to five years can involve significant costs. Beyond the upfront computing costs, one must include expenditures for procurement, deployment, and asset management.

If you’re a business owner, there’s probably a good chance you spent time figuring out the IT needs of your business. It’s not as easy as searching online and picking the cheapest option or the company with the best reviews. The cheap option may not provide the services you need to keep your business at the top of its game, and the best-reviewed business may be too expensive or offer services that are completely unnecessary for your business. To put it simply, if you want to get the most out of your IT support…

There’s a growing trend creeping into organizations of all industries and sizes: Shadow IT. Shadow IT are unauthorized cloud applications employees are using and downloading to perform work-related activities with company data. This can be file-sharing services like Dropbox or surveys such as Zoomerang. The list goes on and on. So what’s the problem? For starters, if you’re in a highly regulated industry like medical or financial services, you’re almost guaranteed to be flagrantly violating data privacy laws or at least flirting with them; and if you’re audited, you could end up facing BIG…

A question we often get is “Why do I need to be on a managed IT plan? Can’t I just pay someone to come out and fix things when they’re broken?” While that’s a legitimate question if we were talking about your washing machine or car, that’s NOT the right approach to a critical and dynamic IT system that your company depends on; you definitely don’t want to wait until something “breaks” before you try and fix a problem. One virus or hacker attack, power loss, electronic component failure, disk space error, or hard…




