Cybersecurity
Managed Security Services
Comprehensive cybersecurity solutions for every SMB
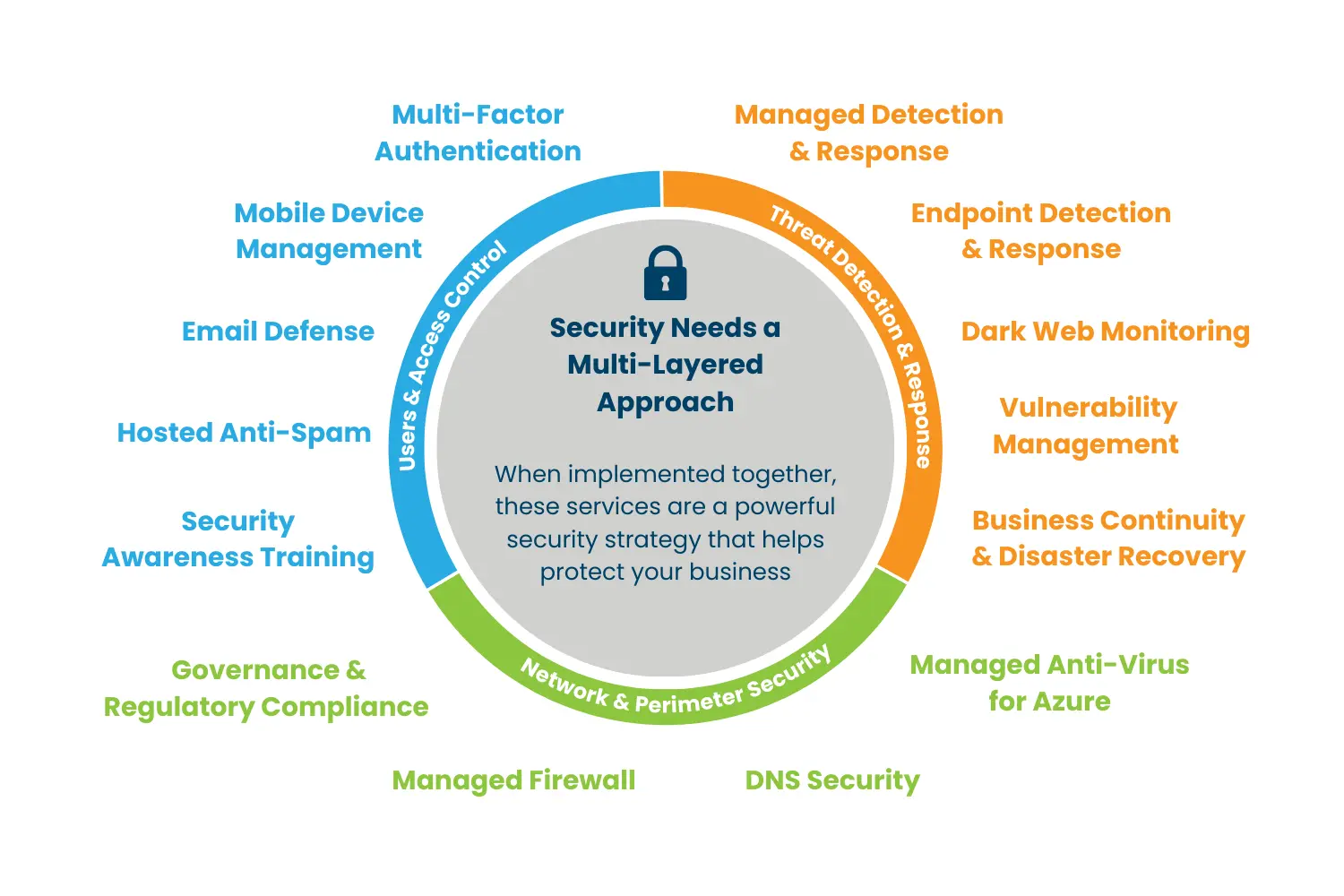
SMBs should have a multi-layered cybersecurity approach
At Dynamic Quest we believe that businesses should have a comprehensive, multi-faceted approach to cybersecurity. We don't provide 'starter kits' because they simply don't work.
Every day, businesses are up against a growing wave of cyberthreats that can throw operations into chaos, compromise sensitive information, and shake customer confidence. The worrying part is cybercriminals show no signs of slowing down.
Free Whitepaper: 2025 Cybersecurity Survival Guide

Cyberattacks are becoming more sophisticated than ever, and small to medium-sized businesses (SMBs) are prime targets. Don’t let your business become another statistic. Our free whitepaper, 2025 Cybersecurity Survival Guide, is full of expert insights and actionable strategies to boost your defenses.
Explore our full suite of managed cybersecurity services
Security assessment
A top-to-bottom review of your organization’s security posture to identify vulnerabilities and provide actionable recommendations to reduce your cyber risk
Next-generation endpoint protection
Advanced solutions designed to protect devices against sophisticated security threats, leveraging AI-augmented threat detection, anti-malware software, endpoint management platforms, and access controls
Cybersecurity awareness training
Teaching your employees how to identify cunning cyberthreats and helping them develop good security habits related to passwords, data management, internet access, and more
Managed firewall
Expert oversight of your firewall infrastructure, including monitoring, updates, and configuration adjustments to fortify your network security
IT regulatory compliance
Stay compliant with industry-specific data privacy regulations such as those set out by HIPAA, PCI DSS, and SOX
Email defense
Includes email filtering to prevent harmful emails from reaching your team’s inbox and data loss prevention policies to stop unauthorized disclosures of sensitive information
Penetration testing
Simulated cyberattacks to uncover weaknesses in your systems and provide actionable insights for threat and vulnerability management
Managed backup and disaster recovery
Reliable data protection and recovery solutions to minimize downtime and safeguard critical business information during disruptions
Managed detection and response
24x7x365 threat monitoring services that include curated threat intelligence and user behavior analytics to detect, analyze, and contain security incidents before they escalate
Governance, risk, and compliance
Designing and implementing a security strategy that fits your risk profile and compliance requirements, with a focus on protocols and procedures pertaining to data classification, remote access controls, and acceptable use
Unified threat management
Combining multiple technologies protecting your network, endpoints, software, and data into one overarching, multilayered defense strategy, which includes intrusion prevention systems, dynamic content filtering, and application intelligence control
Dark web monitoring
Continuous surveillance and reporting of any dark web activities that may be relevant to the organization, which is a useful tool for determining whether your data, domain, and systems have been compromised
The Most Common Cybersecurity Threats to Small and Medium-Sized Businesses
Phishing attacks
Fake emails, messages, and phone calls trick users into revealing sensitive information such as passwords or financial details.
Malware
Distributed denial-of-service
Insider threats
Password attacks
Zero-day vulnerabilities
Why choose Dynamic Quest as your managed security services provider
Partnering with Dynamic Quest brings unparalleled advantages for your business.
24x7x365 protection
Our security experts provide around-the-clock monitoring and are fully prepared to respond to threats at any time of the day.
Cost efficiency
Avoid the expenses associated with an in-house security team by leveraging our vast expertise and resources.
Customized security
We tailor our services to your company’s existing security infrastructure, vulnerabilities, industry compliance standards, and budget.
Peace of mind
Having us at the helm of your security operations means you don’t need to deal with complex security challenges and you can focus solely on your business.
Our vendors
Secure your business with Dynamic Quest
Let Dynamic Quest’s managed security service protect your systems and data from today’s most pressing cyberthreats.